Infoblox and MS Management Permissions
How to avoid using Domain Admin
The NIOS documentation lacks great instructions for granting least-privilege access to use the various MS Management components. As a former Active Directory admin, that bugs me because people get frustrated and end up giving service accounts Domain Admin permissions just to get things working. This post will lay out the necessary permissions for each component and provide PowerShell examples on how to apply them easily.
Warning: I’ve tested these permissions and examples against NIOS 8.4 and Windows Server 2008 R2 through 2019. Your mileage may vary if your environment doesn’t fit those characteristics.
Prerequisites
DNS and DHCP management don’t require targetting domain controllers or even domain joined servers. But it is the most common configuration so our examples will reflect that assumption. If you’re targetting a non-domain joined server, you’ll need to change the user/group references accordingly and modify the PowerShell commands to use their non-AD equivalents.
Infoblox allows you to use a separate service account for each component, but most organizations choose to use one account for simplicity. So we’ll do the same here with a standard AD user account called svc-infoblox.
Most of these components have the choice to be configured in “Read-only” or “Read/Write” mode. For organizations who want to use the features in Read-only mode, I still usually suggest granting the permissions necessary for Read/Write in case they change their mind later. Ironically, it also tends to be harder to grant read-only permissions for these services. The examples here will assume Read/Write mode.
In my testing, no manual changes to the Windows default firewall settings were needed. However, if you have group policy or external firewalls locking things down, you’ll likely need to open things like the dynamic RPC port range between the managing grid member and the target server. See the Deployment Guidelines doc page for details.
DNS
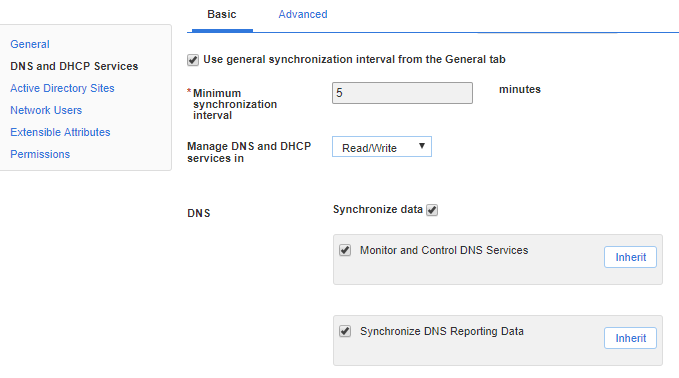
Synchronize Data
This is the core ability to synchronize zone and record data. All we need is membership in DnsAdmins.
Get-ADGroup 'DnsAdmins' | Add-ADGroupMember -Members (Get-ADUser 'svc-infoblox')
Monitor and control DNS Services
This adds the ability to see the status of and start/stop the DNS service on the target machine. It requires full control on the local service control manager and DNS service. We’ll give the permissions to the DnsAdmins group because our service account is already a member.
Make sure to run these on the target server.
# Full control on SCManager for DnsAdmins
$scmSDDL = (&sc.exe sdshow scmanager)[1]
$DnsAdminsSID = (Get-ADGroup DnsAdmins).SID.ToString()
$newSDDL = $scmSDDL.Insert(2, "(A;;KA;;;$DnsAdminsSID)")
&sc.exe sdset scmanager $newSDDL
# Full control on on DNS service for DnsAdmins
$dnsSDDL = (&sc.exe sdshow dns)[1]
$DnsAdminsSID = (Get-ADGroup DnsAdmins).SID.ToString()
$newSDDL = $dnsSDDL.Insert(2, "(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;$DnsAdminsSID)")
&sc.exe sdset dns $newSDDL
Windows Server 2016 and later adds an additional hurdle for controlling services from a non-admin account as described in KB 4457739. We need to exempt the DNS service from the new protection.
$keyName = 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurePipeServers\SCM'
$valName = 'RemoteAccessCheckExemptionList'
$key = Get-Item $keyName
$values = $key.GetValue($valName)
if ('dns' -notin $values) {
$values += 'dns'
Set-ItemProperty $keyName $valName $values -Type MultiString
}
Synchronize DNS Reporting Data
Important: This feature is only compatible with Windows Server 2012 R2 with KB 2919355 or Server 2016 and later. So make sure it’s disabled on anything earlier. See the “Synchronizing DNS Reporting Data” section in the docs for more details.
We need the ability to read the DNS specific event logs. So we’ll add the service account to Event Log Readers.
Get-ADGroup 'Event Log Readers' | Add-ADGroupMember -Members (Get-ADUser 'svc-infoblox')
DHCP
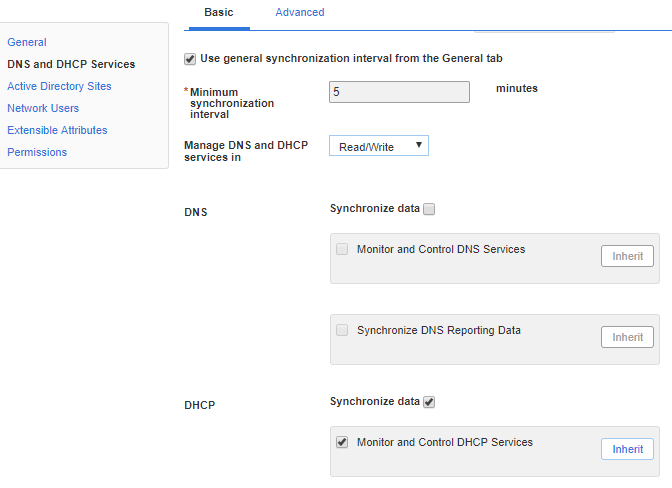
Synchronize Data
This is the core ability to synchronize the scope data. All we need is membership in DHCP Administrators.
Get-ADGroup 'DHCP Administrators' | Add-ADGroupMember -Members (Get-ADUser 'svc-infoblox')
Monitor and control DHCP Services
This adds the ability to see the status of and start/stop the DHCP service on the target machine. It requires full control on the local service control manager and DHCP service. We’ll give the permissions to the DHCP Administrators group because our service account is already a member.
Make sure to run these on the target server.
# Full control on SCManager for DHCP Administrators
$scmSDDL = (&sc.exe sdshow scmanager)[1]
$DhcpAdminsSID = (Get-ADGroup 'DHCP Administrators').SID.ToString()
$newSDDL = $scmSDDL.Insert(2, "(A;;KA;;;$DhcpAdminsSID)")
&sc.exe sdset scmanager $newSDDL
# Full control on on DNS service for DnsAdmins
$dhcpSDDL = (&sc.exe sdshow dhcpserver)[1]
$DhcpAdminsSID = (Get-ADGroup 'DHCP Administrators').SID.ToString()
$newSDDL = $dhcpSDDL.Insert(2, "(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;$DhcpAdminsSID)")
&sc.exe sdset dhcpserver $newSDDL
Windows Server 2016 and later adds an additional hurdle for controlling services from a non-admin account as described in KB 4457739. We need to exempt the DHCP service from the new protection.
$keyName = 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurePipeServers\SCM'
$valName = 'RemoteAccessCheckExemptionList'
$key = Get-Item $keyName
$values = $key.GetValue($valName)
if ('dhcpserver' -notin $values) {
$values += 'dhcpserver'
Set-ItemProperty $keyName $valName $values -Type MultiString
}
Active Directory Sites
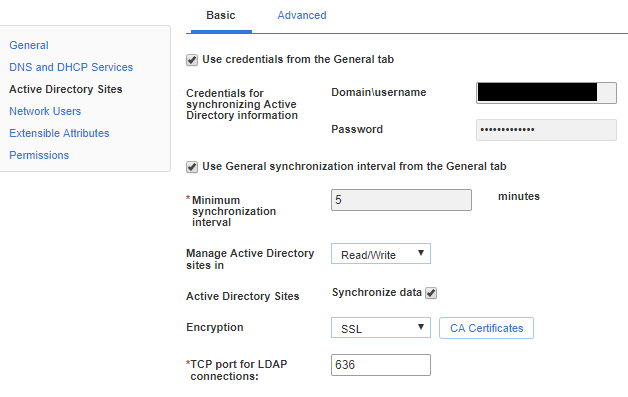
If you plan to use LDAP over SSL (LDAPS), make sure your domain controllers have valid certificates. If the certificates are from an internal PKI infrastructure, make sure the CA certificate has been uploaded to Infoblox as well.
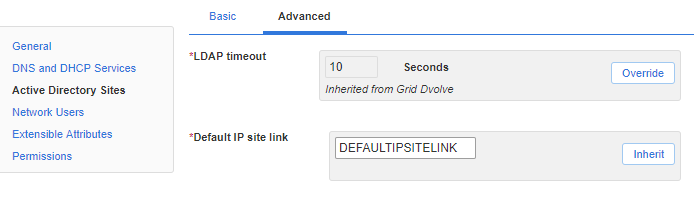
Make sure “Default IP site link” is set to a real site link in your environment even if you don’t plan to create sites directly from Infoblox.
Important: Infoblox will only synchronize sites/subnets with the DC holding the PDC emulator (PDCe) FSMO role. In a multi-domain forest, you should only target the PDCe in the root domain. Some organizations also choose to configure a second DC which FSMO roles would be transferred to in a DR situation. Infoblox will simply ignore it until it becomes the PDCe.
Permissions for Subnets
These permissions will allow Infoblox to assign/unassign subnets to/from existing sites.
CN=Subnets,CN=Sites,<Configuration Naming Context>
- Applies to: This object only
- Create Subnet objects
- Delete Subnet objects
- Applies to: Descendant subnet objects
- Read all properties
- Write all properties
- Delete
- Delete subtree
PowerShell example:
$cfgContext = (Get-ADRootDSE).configurationNamingContext
$target = "AD\svc-infoblox" # group or user reference
&dsacls.exe "CN=Subnets,CN=Sites,$cfgContext" /G "$($target):CCDC;subnet"
&dsacls.exe "CN=Subnets,CN=Sites,$cfgContext" /I:S /G "$($target):RPWPSDDT;;subnet"
Permissions for Sites
These permissions will allow Infoblox to create/delete/rename site objects. On creation, the new site will be associated with the “Default IP site link” mentioned earlier. In these examples, we’ll assume that is DEFAULTIPSITELINK.
CN=Sites,<Configuration Context>
- Applies to: This object only
- Create Site objects
- Delete Site objects
- Applies to: Descendant Site objects
- Read all properties
- Write all properties
- Delete
- Delete subtree
- Create all child objects
CN=<Default SiteLink>CN=IP,CN=Inter-Site Transports,CN=Sites,<Configuration Context>
- Read/Write siteList
PowerShell example:
$cfgContext = (Get-ADRootDSE).configurationNamingContext
$target = "AD\svc-infoblox" # group or user reference
$defaultSiteLink = "CN=DEFAULTIPSITELINK,CN=IP,CN=Inter-Site Transports,CN=Sites,$cfgContext"
&dsacls.exe "CN=Sites,$cfgContext" /G "$($target):CCDC;site"
&dsacls.exe "CN=Sites,$cfgContext" /I:S /G "$($target):RPWPSDDTCCLCRC;;site"
&dsacls.exe $defaultSiteLink /G "$($target):RPWP;siteList"
Network Users
For this, Infoblox is just reading the Security event log on the target domain controller. So we need membership in Event Log Readers.
Get-ADGroup 'Event Log Readers' | Add-ADGroupMember -Members (Get-ADUser 'svc-infoblox')
